Can you trust your new VPN? Here's an easy way to investigate

There are plenty of quality big-name VPN providers out there, but sometimes, when you're shopping for a new service, someone new might catch your eye.
Maybe it's the low prices. Perhaps it's the lengthy feature list, or the big promises about how this VPN beats the rest in just about every way. You're so tempted to sign up on the spot, and yet, something feels wrong...
You're right to be cautious. Use any VPN and you're trusting it with your most important online activities. Should you really do that if it's a tiny provider that you only discovered ten minutes ago, and a quick Google search gives you no useful background information? We'd say, probably not.
That doesn't mean you should only ever use the most well renowned VPNs. But if you're looking at someone brand new, and you've no idea who runs the company, who's behind it, if it's safe or a total scam, then it pays to do a little investigating. In this article we'll explain how you can look into any provider, find out more about the business, and see if this is a VPN that deserves your trust.
- Looking for a bargain? Here are today's best VPN deals on the biggest names
Explore the VPN website
Start your investigations at the VPN website, with whatever the provider tells you. If there's an About Us page, read it, look for names of founders, companies, locations or other identifying details.
Check the Privacy Policy and Terms of Use pages, too. They sometimes use different company names, perhaps giving you the parent company.
Because these are legal documents, they might also tell you which national laws they're following, an indication of where the provider is based. Look for a line such as 'the policy shall be governed by and construed in accordance with the law of Seychelles.'
Pay a visit to the provider's social media accounts. These may have more details about the company.
Look for contact email addresses which aren't the provider's website domain. Instead of support@suspectvpn.com, for instance, they might be suspectvpn@gmail.com, or suspectvpn@anothercompany.com. If you see a general email address from Gmail or another big service, run a web search, find out where else it's mentioned. If the address uses another company's domain, visit it to find out more.
Try entering the VPN domain at the Wayback Machine to see how it looked a year or two ago. It's possible you'll find important company details which have since been dropped.

Check the app stores
If your target service has mobile VPN apps, it's well worth visiting their Google Play and App Store pages. These often have useful information on a provider, and sometimes include details you won't find on the website.
Start by browsing each page for anything that tells you more about the company. What's the name of the developer? Is there a website link? If there's a privacy policy, where it is hosted? What is the contact email address?
These details won't always match up. The developer name might be different to the VPN, for instance. That doesn't necessarily mean there's a problem: the VPN may not have the ability to develop an iOS app, perhaps, so they're reselling someone else's product. But visit the developer's website, anyway, and search for its name online, just to see what comes up.
Run more web searches for any other new details you've discovered, too, especially alternative contact email addresses. Sometimes the real VPN owner will use the same address to set up multiple brands, and the search results may give you important clues about what's going on.
Who registered the website domain?
Finding out who registered your VPN's website domain could point you to its real owner. Enter it (and any related domains you found on the app store pages) at Who.is to look for clues.
As earlier, run a web search for any new names, companies or contact emails you see in the registration records. They could point you to the people behind the provider, or show you how they're linked to other VPNs.
We regularly see names and email addresses replaced by blanket 'withheld for privacy reasons' warnings. Don't read too much into that. Sure, it might mean someone's trying to keep their VPN ownership secret. But they could also be looking to avoid spam, a big problem for everyone who registers a domain.
Windscribe - an example of a perfectly reputable provider - uses a privacy service to keep its registration email private, for instance. But that means nothing: it's also a very open, honest and private VPN.
The Who.is records also show when the domain was first registered, a small but interesting detail. If the website says the VPN has years of experience but the domain was registered last month, that might be a problem.
The Registrar Info section tells you which company is managing the domain, too. If this is GoDaddy, Namecheap or some other big international corporation, it won't tell you much. But if it's someone smaller, perhaps a provider in Singapore or China, it might give a clue to the provider's real location.
Advanced tricks
Some VPN providers are very good at hiding their real identity, and a standard investigation might not turn up anything useful. But don't give up just yet: we've some advanced tricks which might help...
Hacker Target's Reverse IP Lookup finds sites sharing the same web server as the domain.
We've used this to find providers hosting multiple related sites from their dedicated server. You might see the company website of the real owner, for instance, along with all the other VPN sites they're running.
If nothing else, you'll get an idea of how much the VPN is spending on hosting. If the provider isn't sharing with other sites, it's likely using a powerful dedicated server, which is good; if it's sharing with hundreds of random URLs, it's probably using cheap shared hosting, which is bad.
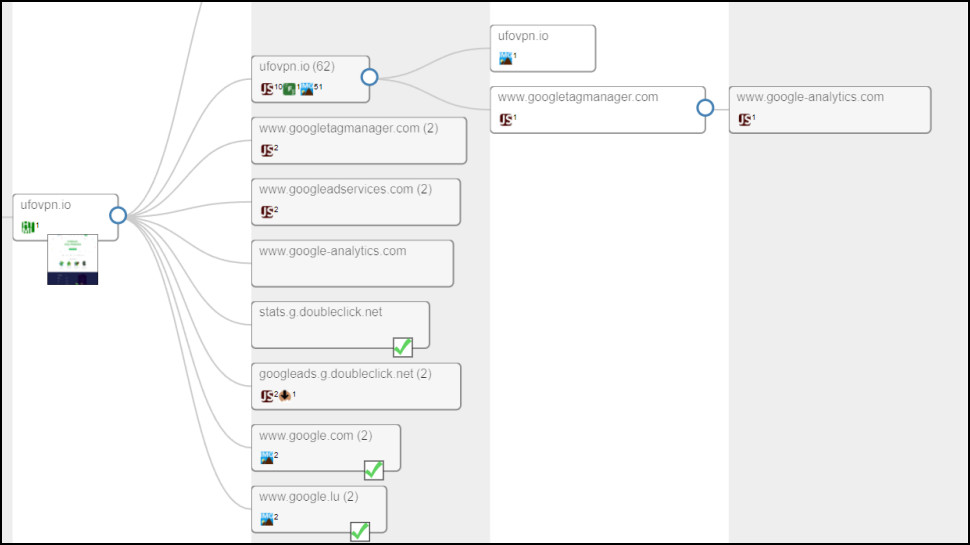
Lookyloo is a powerful web forensics tool which displays all the domains a web page contacts when it loads images, scripts and more.
Enter a VPN URL and we've sometimes found it links to another domain used by the real VPN owner, or at least points us in the right direction.
But again, even if this doesn't help identify who is behind the VPN, there's still useful detail here. If the site links to 27 tracker or ad sites, for instance, Lookyloo will let you know, and that could justify ignoring the VPN all on its own.
- PC user? These are the best Windows 10 VPNs
- Or for those that prefer Apple, these are the best Mac VPNs
- We’ve rounded up the fastest VPNs for outright speed
from TechRadar - All the latest technology news https://ift.tt/3HlBp2s

Post a Comment